ISO / IEC 27001:2022
ISO/IEC 27001 Certification
ISO/IEC 27001 is the internationally recognized standard for Information Security Management Systems (ISMS). It provides a structured framework to protect your organization's sensitive information through a systematic approach to risk management and security controls.
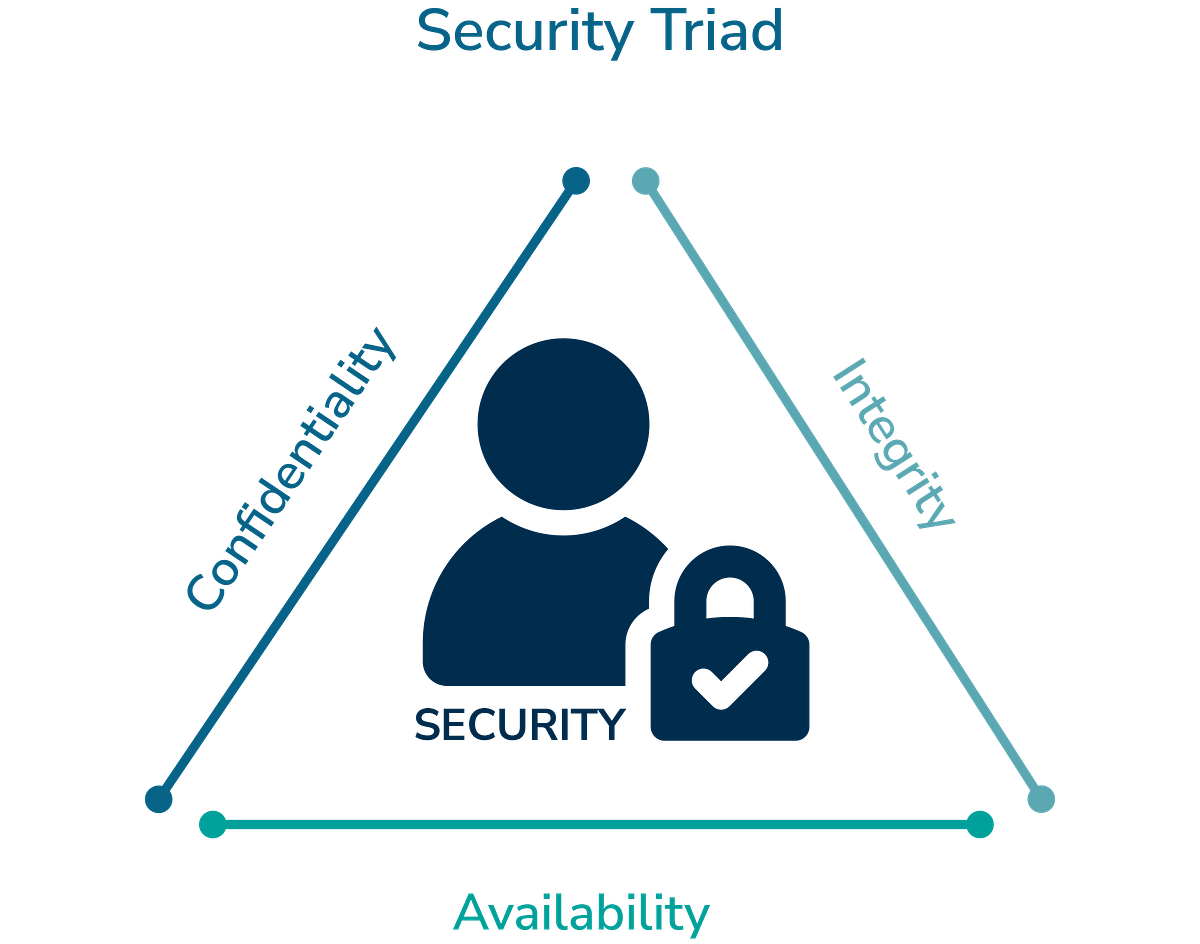
Core Principles
ISO/IEC 27001 ensures your information security framework addresses:
-
Confidentiality: Information is accessible only to authorized individuals.
-
Integrity: Information accuracy and completeness are safeguarded and modifications occur only by authorized users.
- Availability: Authorized users have timely access to information and assets needed to operate effectively.
What Certification Demonstrates
Achieving ISO/IEC 27001 certification confirms that your organization has:
- Protected information from unauthorized access
-
Ensured the accuracy and integrity of information
-
Assessed risks and mitigated breach impacts
-
Undergone independent assessment against a rigorous international standard grounded in industry best practices unlike many superficial certifications often issued rapidly with minimal verification, Xiligent ensures that your certification upholds full compliance with true international standards, providing genuine operational readiness and control effectiveness.

Domains Covered
ISO/IEC 27001 spans essential security domains including:
Information Security Policy
Asset management
Human resources security
Physical and environmental security
Communications and operations management
Access control
Information systems acquisition, development, and maintenance
Information security incident management
Business continuity management
Compliance Organization of information security
How Xiligent Supports Your ISO/IEC 27001 Journey
We guide you through scoping, risk assessment, control implementation, and continuous improvement. Our tailored ISMS solutions align with your business goals and prepare you for successful external audits. Xiligent builds more than just documentation—we create sustainable security frameworks that support long-term growth and assurance.
Business Benefits
Approach to get you certified

Resources

Building Trusted, Responsible AI Compliance for Modern Enterprises with AI 42001 : 2023
ISO 42001:2023 is the first international standard specifically dedicated to the management of artificial-intelligence (AI) systems. It defines requirements and guidance for establishing, implementing, maintaining and continually improving an AI Management System (AIMS) within an organisation. (Microsoft Learn) The standard covers the full lifecycle of AI systems — from conception, design, development, deployment, monitoring, through […]

Essential Steps for Implementing DPDP Regulations Efficiently
The rise of data breaches and privacy concerns, regulations like the Data Protection and Digital Privacy (DPDP) are crucial. Implementing these regulations can seem daunting, but with the right approach, it can be a smooth process. This blog post will guide you through essential steps for implementing DPDP regulations efficiently. Understanding DPDP Regulations Before diving […]

Understanding GDPR Compliance for Your Business Needs
In today’s digital world, data privacy is more important than ever. The General Data Protection Regulation (GDPR) is a law that protects personal data in the European Union. If your business handles personal data, understanding GDPR compliance is crucial. This post will guide you through the essentials of GDPR, its requirements, and how to ensure […]

How Xiligent Simplifies Your Privacy Assessment Process
Privacy is power. With data breaches and privacy regulations on the rise, businesses must take privacy assessments seriously. However, the process can often feel overwhelming. This is where Xiligent comes in. Xiligent offers a streamlined approach to privacy assessments, making it easier for organizations to manage their data privacy needs. In this post, we will […]
ISO/IEC 27001 is the global standard for establishing and operating an ISMS.
Information Security Management System
SaaS, AI, fintech, healthtech, and logistics companies | Consumer-facing digital platforms and marketplaces | IT/ITES and BPO/KPO service providers | D2C brands collecting user data | Cloud-native or hybrid-cloud businesses | Companies entering global markets or selling to regulated industries | Even early-stage companies benefit when enterprise buyers expect formal security assurance.
What is the latest version of ISO/IEC 27001? Is the older 2013 version still valid?
+The latest version is ISO/IEC 27001:2022. It modernises the Annex A controls, aligns with current threat models, and introduces clearer organisational, technological, and cloud-relevant controls. The previous version, ISO/IEC 27001:2013, is now being phased out. Certification bodies have set transition deadlines (generally late 2025) by which all organisations must migrate to the 2022 version. If you are seeking certification now, you will be certified against ISO/IEC 27001:2022.
What does ISO/IEC 27001 implementation involve?
+Typical activities include risk assessment, control selection, policy drafting, technical safeguards, employee training, operational evidence collection, and an internal audit before the certification audit.
Does ISO/IEC 27001 work for cloud-native or small organisations?
+Yes. ISO/IEC 27001 is widely adopted by SaaS, fintech, logistics, AI, and digital enterprises - even those with fully cloud-based environments.